| PAN | LAN | MAN | WAN | |
| Standards | Bluetooth | 802.11 | 802.11 | GSM, CDMA, Satellite |
| Speed | < 1 Mbps | 11 to 54 Mbps | 10-100+ Mbps | 10 Kbps-2 Mbps |
| Range | Short | Medium | Medium-Long | Long |
| Applications | Peer-to-Peer | Enterprise | Last Mile Access | Mobile Data |
Comparing a WLAN to LAN
| Characteristic | 802.11 Wireless LAN | 802.3 Ethernet LANs |
| Physical Layer | Radio Frequency (RF) | Cable |
| Media Access | Collision Avoidance | Collision Detection |
| Availability | Anyone with a radio NIC in range of an access point | Cable connection required |
| Signal Interference | Yes | Inconsequential |
| Regulation | Additional regulation by local authorities | IEEE standard dictates |
WLAN Characteristics
Wireless LAN Standards
Terminology
When a standard uses OFDM, it will have faster data rates.
DSSS is simpler than OFDM, so it is less expensive to implement.
Wi-Fi Certification
provided by the Wi-Fi Alliance (http://www.wi-fi.org), a global, nonprofit, industry trade association devoted to promoting the growth and acceptance of WLANs.
Internationally, the three key organizations influencing WLAN standards are:
The ITU-R regulates the allocation of the RF spectrum and satellite orbits. These are described as finite natural resources that are in demand from such consumers as fixed wireless networks, mobile wireless networks, and global positioning systems.
The IEEE developed and maintains the standards for local and metropolitan area networks with the IEEE 802 LAN/MAN family of standards. IEEE 802 is managed by the IEEE 802 LAN/MAN Standards Committee (LMSC), which oversees multiple working groups. The dominant standards in the IEEE 802 family are 802.3 Ethernet, 802.5 Token Ring, and 802.11 Wireless LAN.
Although the IEEE has specified standards for RF modulation devices, it has not specified manufacturing standards, so interpretations of the 802.11 standards by different vendors can cause interoperability problems between their devices.
The Wi-Fi Alliance is an association of vendors whose objective is to improve the interoperability of products that are based on the 802.11 standard by certifying vendors for conformance to industry norms and adherence to standards. Certification includes all three IEEE 802.11 RF technologies, as well as early adoption of pending IEEE drafts, such as 802.11n, and the WPA and WPA2 security standards based on IEEE 802.11i.
The roles of these three organizations can be summarized as follows:
AP’s
CSMA/CA
it is expensive to make wireless NICs that can transmit and receive at the same time, so radio devices do not detect collisions. Instead, WLAN devices are designed to avoid them.
Access points oversee a distributed coordination function (DCF) called Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA)
This simply means that devices on a WLAN must sense the medium for energy (RF stimulation above a certain threshold) and wait until the medium is free before sending.
Because all devices are required to do this, the function of coordinating access to the medium is distributed. If an access point receives data from a client station, it sends an acknowledgement to the client that the data has been received. This acknowledgement keeps the client from assuming that a collision occurred and prevents a data retransmission by the client.
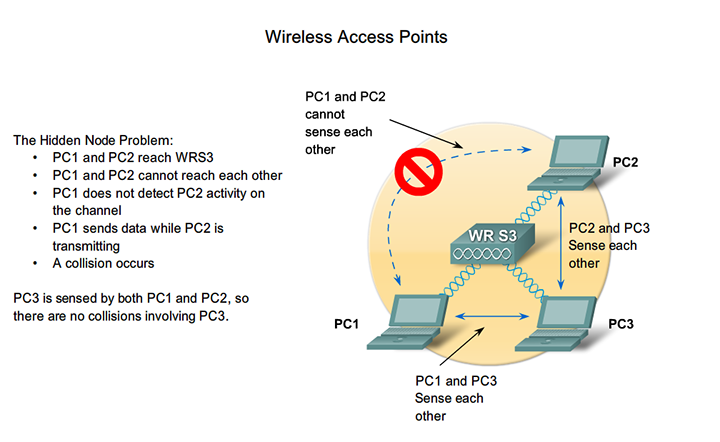
RF signals attenuate. That means that they lose their energy as they move away from their point of origin. Think about driving out of range of a radio station. This signal attenuation can be a problem in a WLAN where stations contend for the medium.
Imagine two client stations that both connect to the access point, but are at opposite sides of its reach. If they are at the maximum range to reach the access point, they will not be able to reach each other. So neither of those stations sense the other on the medium, and they may end up transmitting simultaneously. This is known as the hidden node (or station) problem.
One means of resolving the hidden node problem is a CSMA/CA feature called request to send/clear to send (RTS/CTS). RTS/CTS was developed to allow a negotiation between a client and an access point. When RTS/CTS is enabled in a network, access points allocate the medium to the requesting station for as long as is required to complete the transmission. When the transmission is complete, other stations can request the channel in a similar fashion. Otherwise, normal collision avoidance function is resumed.
Parameters for Wireless Endpoints
1.WLAN protocols: 802.11a, b, g, or n.
if all the clients connect to an access point with 802.11g, they all enjoy the better data rates provided.
For an access point to support 802.11a as well as 802.11b and g, it must have a second radio to operate in the different RF band.
2.
A shared service set identifier (SSID) is a unique identifier that client devices use to distinguish between multiple wireless networks in the same vicinity. Several access points on a network can share an SSID. The figure shows an example of SSIDs distinguishing between WLANs, each which can be any alphanumeric, case-sensitive entry from 2 to 32 characters long.
3
The IEEE 802.11 standard establishes the channelization scheme for the use of the unlicensed ISM RF bands in WLANs. The 2.4 GHz band is broken down into 11 channels for North America and 13 channels for Europe. These channels have a center frequency separation of only 5 MHz and an overall channel bandwidth (or frequency occupation) of 22 MHz.
The 22 MHz channel bandwidth combined with the 5 MHz separation between center frequencies means there is an overlap between successive channels. Best practices for WLANs that require multiple access points are set to use non-overlapping channels. If there are three adjacent access points, use channels 1, 6, and 11. If there are just two, select any two that are five channels apart, such as channels 5 and 10. Many access points can automatically select a channel based on adjacent channel use. Some products continuously monitor the radio space to adjust the channel settings dynamically in response to environmental changes.
802.11 Topologies
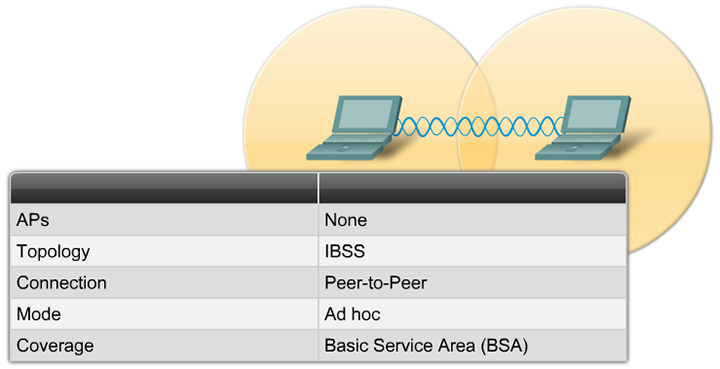
Basic service set
The basic service set (BSS) is defined in the standard as a group of stations that communicate with each other.
There are two types of BSS:
Every BSS has an identification (ID) called the BSSID, which is the MAC address of the access point servicing the BSS.
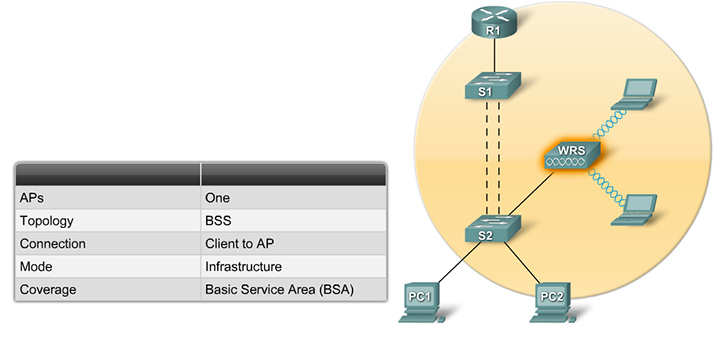
Extended service set
An extended service set (ESS) is a set of connected BSSs. Access points in an ESS are connected by a distribution system. Each ESS has an ID called the SSID which is a 32-byte (maximum) character string.
When a single BSS provides insufficient RF coverage, one or more can be joined through a common distribution system into an extended service set (ESS). In an ESS, one BSS is differentiated from another by the BSS identifier (BSSID), which is the MAC address of the access point serving the BSS. The coverage area is the extended service area (ESA).
Common Distribution System
The common distribution system allows multiple access points in an ESS to appear to be a single BSS. An ESS generally includes a common SSID to allow a user to roam from access point to access point.
Cells represent the coverage area provided by a single channel. An ESS should have 10 to 15 percent overlap between cells in an extended service area. With a 15 percent overlap between cells, an SSID, and non-overlapping channels (one cell on channel 1 and the other on channel 6), roaming capability can be created.
Summary
Client and Access Point Association
- Beacons - Frames used by the WLAN network to advertise its presence.
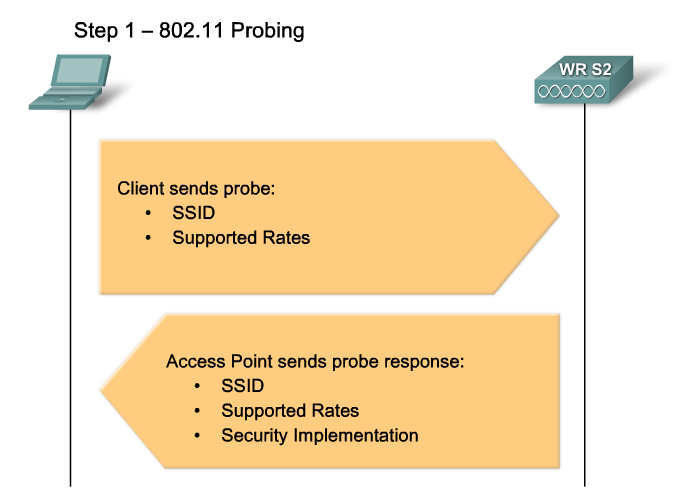
- Probes - Frames used by WLAN clients to find their networks.
The primary purpose of the beacon is to allow WLAN clients to learn which networks and access points are available in a given area, thereby allowing them to choose which network and access point to use. Access points may broadcast beacons periodically.
- Authentication - A process which is an artifact from the original 802.11 standard, but still required by the standard.
Clients search for a specific network by sending a probe request out on multiple channels. The probe request specifies the network name (SSID) and bit rates. A typical WLAN client is configured with a desired SSID, so probe requests from the WLAN client contain the SSID of the desired WLAN network.
If the WLAN client is simply trying to discover the available WLAN networks, it can send out a probe request with no SSID, and all access points that are configured to respond to this type of query respond. WLANs with the broadcast SSID feature disabled do not respond.
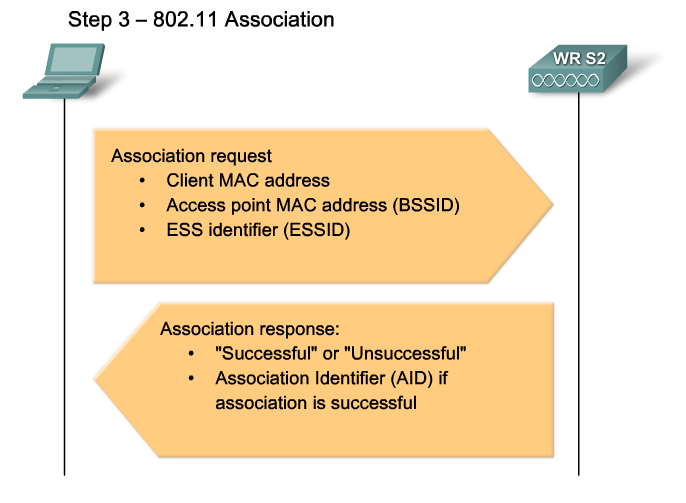
- Association - The process for establishing the data link between an access point and a WLAN client.
802.11 was originally developed with two authentication mechanisms. The first one, called open authentication, is fundamentally a NULL authentication where the client says "authenticate me," and the access point responds with "yes." This is the mechanism used in almost all 802.11 deployments.
A second authentication mechanism is referred to as shared key authentication. This technique is based on a Wired Equivalency Protection (WEP) key that is shared between the client and the access point. In this technique, the client sends an authentication request to the access point. The access point then sends a challenge text to the client, who encrypts the message using its shared key, and returns the encrypted text back to the access point. The access point then decrypts the encrypted text using its key and if the decrypted text matches the challenge text, the client and the access point share the same key and the access point authenticates the station. If the messages do not match, the client is not authenticated.
Although shared key authentication needs to be included in client and access point implementations for overall standards compliance, it is not used or recommended. The problem is that the WEP key is normally used to encrypt data during the transmission process. Using this same WEP key in the authentication process provides an attacker with the ability to extract the key by sniffing and comparing the unencrypted challenge text and then the encrypted return message. Once the WEP key is extracted, any encrypted information that is transmitted across the link can be easily decrypted.
This stage finalizes the security and bit rate options, and establishes the data link between the WLAN client and the access point. As part of this stage, the client learns the BSSID, which is the access point MAC address, and the access point maps a logical port known as the association identifier (AID) to the WLAN client. The AID is equivalent to a port on a switch. The association process allows the infrastructure switch to keep track of frames destined for the WLAN client so that they can be forwarded.
Once a WLAN client has associated with an access point, traffic is now able to travel back and forth between the two devices.
Z este radical din A adica suprafata
Deci pentru o suprafata de 500 m2
R este 15.8 metri
Z este 22,3 metri
![wlan[5] wlan[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiUP5Xi1mbABZC3dWe1OM5yffAkCOiZiwzUhlgjuNyn3zVSrwx7cfUiS_w-01u_Oygam_K0dYn3GtvUejYPbZJkzJjsDSh0vvK4FnNMHWBiwCzqeVCYbl108uxWMI5sYZ-CLBy9unV5T3ki/?imgmax=800)





No comments:
Post a Comment